Design > Security
Release Information
| Project: | EGADSS |
|---|---|
| Internal Release Number: | $Revision: 1.4 $ $State:
Exp $ |
| Related Documents: | Design document |
Overview
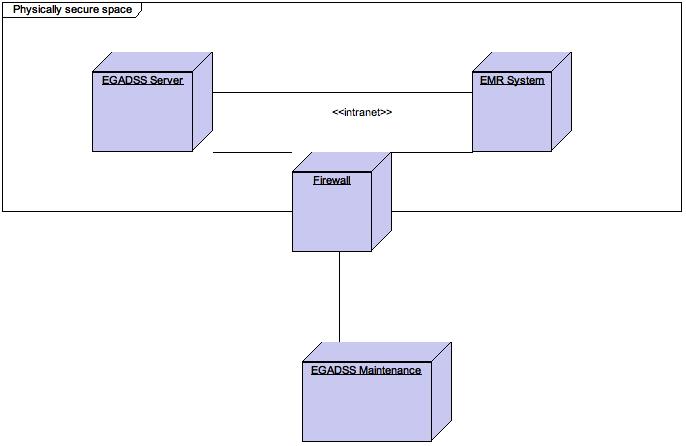
This document elaborates on all known security threats and specifies all security enhancing mechanisms to be implemented. The document is structured according to the physical deployment model in the security deployment model below.
The architecture comprises the EGADSS server (the actual decision support system) and the EMR System (the physician's Electronic Medical Record system - not provided by the EGADSS team). There is another external node (EGADSS Maintenance) to monitor the operations of the EGADSS server and update the guideline base. (No confidential data will be monitored).
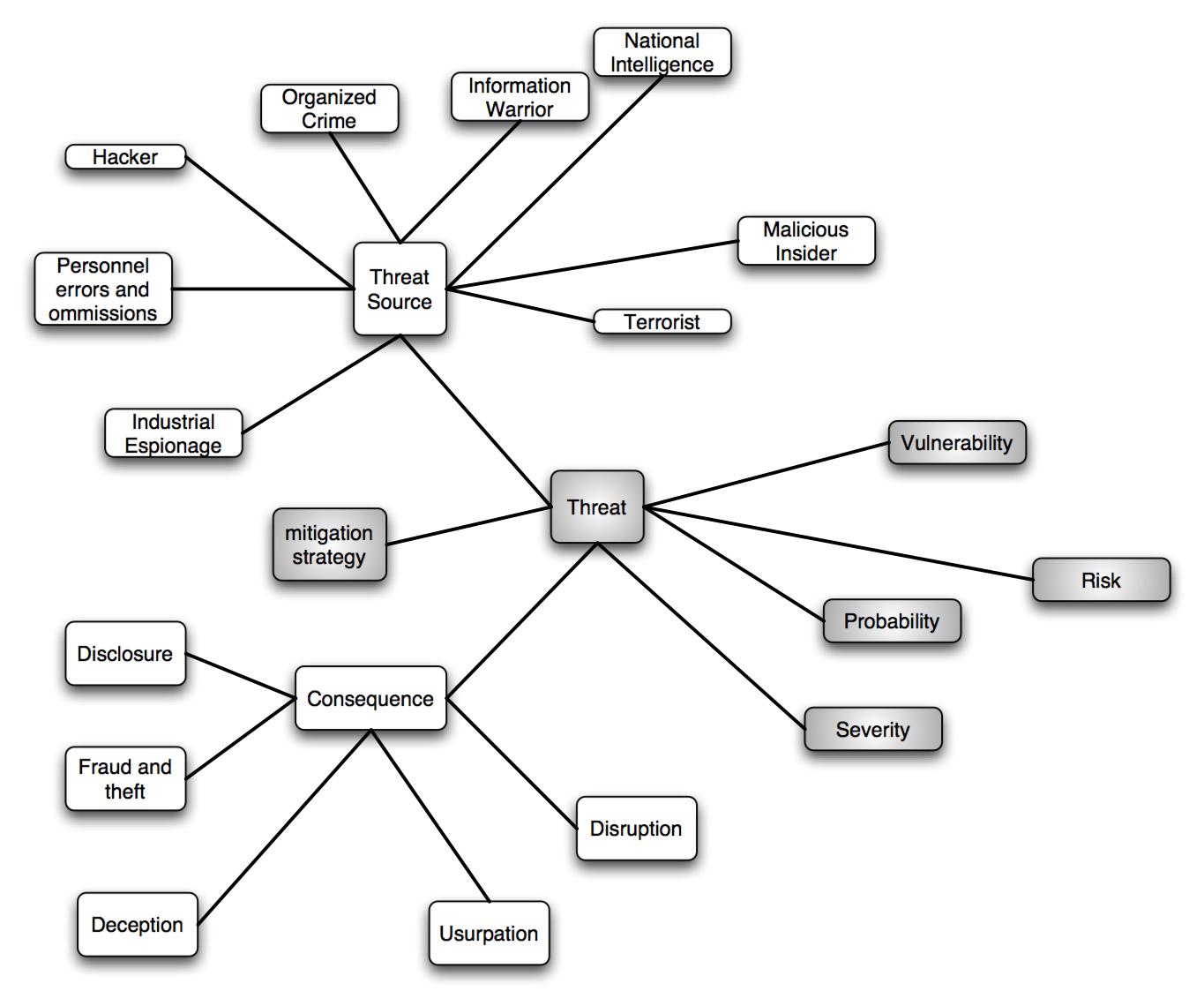
Security Threat Analysis (by
computational node)
- 1. EGADSS Server
Threats:
| Threat # | Source | Vulnerability | Consequence | Mitigation strategy | Probability | Severity | Risk |
|---|---|---|---|---|---|---|---|
| 1 | Hacker | data transmission
between server and EMR system |
disclosure |
|
very low | high | low |
| 2 | Malicious insider |
compromising EGADSS
server to intercept data |
disclosure |
|
very low | high | low |
| 3 | Malicious insider |
load wrong guidelines
into EGADSS server |
Usurpation, disruption |
|
very low | high | low |
| 4 | Personnel errors and ommissions |
accidentally leave door
to server room open |
disclosure theft of device |
|
very low | low (no data persisted) |
low |
| 5 | Hacker | load wrong guidelines
into EGADSS server using the maintenance interface |
Usurpation, disruption |
|
very low | high | low |
- 2.
EMR System